My projects
HSM-Backed Cryptographic Signing Service
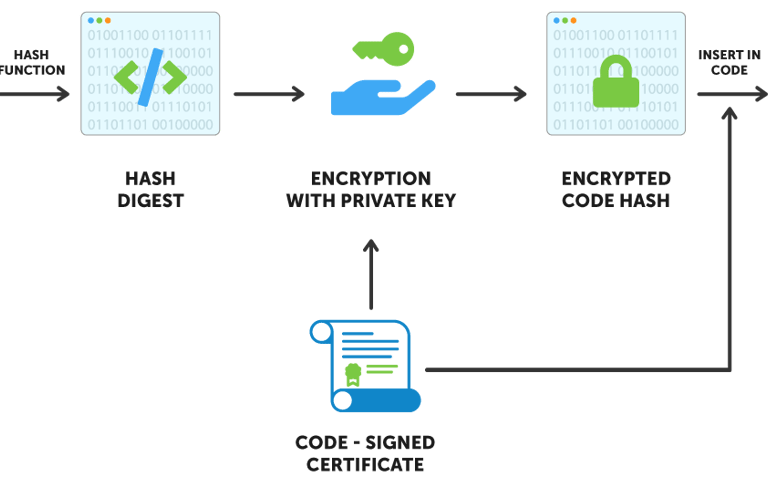
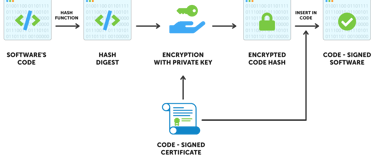
Designed and co-developed a secure, cloud-native signing service hosted in AWS Lambda to meet company-wide code signing requirements across Windows, macOS, iOS, Linux, and other delivery platforms. The service uses a dedicated IAM role with exclusive kms:Sign permissions on a tightly controlled KMS key, enforced via restrictive key policies that prevent any other user or role from viewing sensitive key material or performing signing operations. Requests are routed through a company subdomain and protected with OIDC or JWT verification depending on the client, ensuring strong authentication and authorization. Every stage of the API execution logs events to create a complete, immutable ledger of all sign operations, supporting auditability and compliance. The service is paired with an observability dashboard to monitor health, usage patterns, and operational metrics, enabling proactive maintenance and security oversight.
Kubernetes TTL Enforcement System
Developed and deployed a Kubernetes-native TTL enforcement system in EKS to minimize pod state drift and maintain deployment integrity. The solution consists of four key components:
TTL Controller Service – Automatically enforces expiration times on targeted resources, triggering their removal and allowing Kubernetes to recreate them in a known-good state.
Exec Webhook – Applies TTL annotations to pods whenever a user initiates an exec session, ensuring that manual intervention triggers a refresh cycle.
OPA Policy Enforcement – Protects TTL annotations from unauthorized changes, allowing only cluster administrators and the webhook’s service account to modify them.
Namespace Restriction – Ensures that namespaces housing any TTL Controller components are accessible only to cluster administrators, preventing unauthorized interaction with the enforcement stack.
This architecture ensures that once a pod has been accessed interactively, it cannot persist in an unverified or potentially altered state, thereby reducing configuration drift. By combining admission control, policy enforcement, and automation, the TTL Controller strengthens compliance, operational hygiene, and cluster reliability.


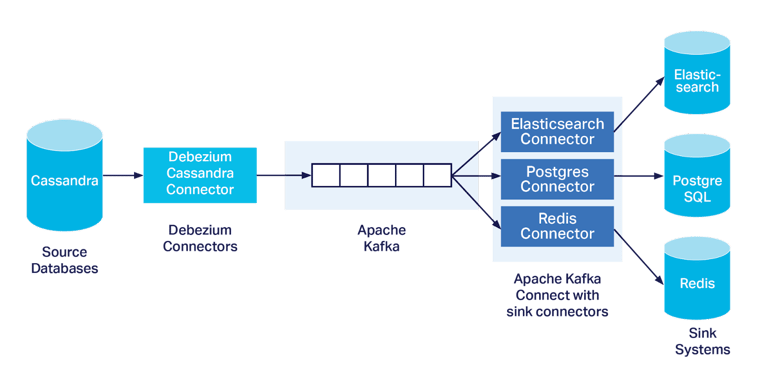
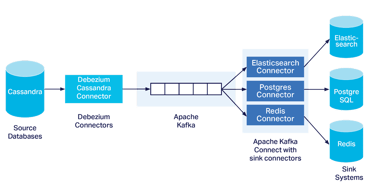
Kafka-Based CDC Ingestion Pipeline
Designed and implemented a distributed CDC ingestion system to replicate and enrich database changes in near real-time. The architecture featured a distributed Kafka Connect producer colocated with the source database’s service, streaming changes to an AWS-managed Kafka cluster. A centralized Kafka Connect consumer processed these events, writing them to Amazon S3 for long-term storage and routing them to an AWS Lambda function for enrichment. The enriched data was then loaded into the company’s Snowflake-based cloud data lake, where it was orchestrated into a network of downstream databases, maintaining near real-time consistency with the source database. This pipeline provided a resilient, scalable foundation for analytics, reporting, and operational systems, ensuring high data fidelity across the organization.